
DEMOKRATIAN, which comes from the Esperanto word for "democracy", is a web application that allows different types of online voting. All registered members will be able to vote in a simple way with the security that their vote is secret.
DEMOKRATIAN is free software under agpl-3.0 license (GNU Affero General Public License) so you are free to install and use it at no cost, but if you need technical support or something special we can make you a quote.
DEMOKRATIAN is in full development, and it is being used or has been used for voting in many sites some of which you can see in this list
(List of sites that have used or are using DEMOKRATIAN).
DEMOKRATIAN allows, in addition to making votes through Internet, to make simultaneous votes in "ballot box" (in person) since it allows to see in real time if a user has voted online and to prevent the vote to those who make it in person.
MAIN CHARACTERISTICS
It is written in PHP programming language and uses a MySQL database so it can be installed and used in most web servers.
When designing the application, these have been the main criteria and functionalities:
- Ease of installation and use, both by voters and by voting administrators.
- Non-traceability of the vote, your vote is secret and no one can know how you voted (except for the debate type of voting, where you can change the direction of your vote as the debate progresses).
- An easy management of voters, so that the administrator can process the voter lists and they can also vote according to the type of vote that we have chosen if they are members/associates or supporters.
- The platform allows different voting areas, you will be registered in a province and municipality, and you can vote in all those provincial and municipal consultations that are created, you can also participate in the consultations of your Autonomous Community, and in the State ones. These working groups can also be state, regional or provincial and can be moderated or open.
- It allows several types of voting, currently there are 4 types of voting. You can choose between:
- Weighted voting (Primaries, Borda or Dowdall recount).
- SUTV. The Single Transferable Vote is a voting system designed to measure the will of the voters more accurately than the conventional vote.
- Survey. Allows you to choose one or more options among several. It is a vote that does not have any type of weighting.
- Debate. This type of voting is a mixed formula of forum and voting in which you can post short comments that appear on a facebook-style board and also, if needed, vote on one or more questions. The user will be able to modify his vote as the debate progresses if he changes his mind. This system does not ensure the non-traceability of the vote, i.e., if someone accesses the database could get to see what a user has voted, also does not implement any of the security measures described below as the voter can see at all times his vote.
- El sistema es compatible con voto en urna y voto online al mismo tiempo ya que permite comprobar si una persona ha votado online, e impedir el voto online si lo hace presencialmente (en urna). Además, para facilitar el posterior recuento si el voto es ponderado, se puede incluir los votos por parte de los interventores en el sistema de forma manual quedando registrados los votos procedentes de urna así como los interventores involucrados por si hay que realizar controles posteriores.
If you have read the information on the home page, you can start reading here
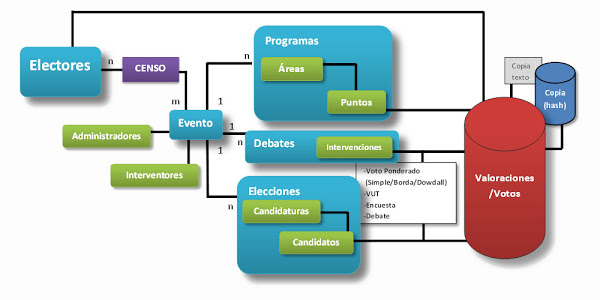
SIMPLIFIED SCHEME and DATA MODEL:

SECURITY, PRIVACY and VERIFIABILITY ISSUES
Absolute security in online voting does not exist, but we have tried to reduce the possibilities of fraudulent use of the platform as much as possible.
On the one hand, the application is aimed at censuses, i.e., only people who are registered can vote, therefore, a fundamental part is to have quality and reliable censuses. It is of little use to have the most secure platform in the world if its census allows unwanted or non-existent people to vote.
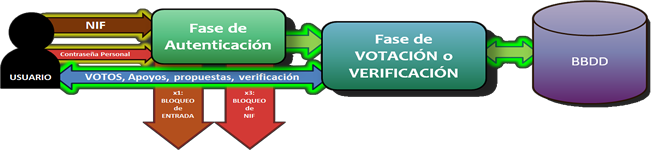
Moreover, the vote is absolutely separated from the voter, i.e. in the database where the votes are stored both data are separated and there is no possibility of linking one data with another. Unlike other voting systems that maintain this data linkage and therefore need complicated encryption systems to avoid problems. In this sense, the system has been created thinking of traditional voting models in which once you put your vote in the ballot box it cannot be modified nor can it be known that the voter has voted (although for the sake of individual verifiability there is a possibility that does not compromise privacy, which is explained below).
Transparency has been prioritized above all, anyone can see that the votes are what they are and can be listed directly from the database without the need for complicated programs or decryption systems that generate a lot of insecurity for the user with low knowledge because it is not clear that the algorithms can not be changing data. In fact, when the voting results are activated, any voter will be able to see all the votes that are in "the virtual ballot box" and by means of a code that is automatically generated when voting and that the user can save at that moment, he will be able to verify that his vote is still there, has not been altered and has been correctly counted.
To prevent votes from being illegally entered into the database, several security systems have been created, on the one hand a second copy of the data is saved, this time encrypted in a unidirectional way with the SHA-256 algorithm, then by comparing data is checked if there are differences.
In addition, a third copy (in a separate file and with restricted access) of the data is stored on the server itself so that if someone has access to the database, a copy with more difficult access would remain.
Additionally, a hash of a secret combination of the last 5 votes is stored in each vote that allows, at the end of the vote, a new verification of the integrity of the data.
Finally, the system has another layer of security, highly advisable for the sake of transparency, which can also be enabled by the administrator, and is the sending of an anonymous mail with each vote to independent auditors (which logically will be limited in number), that is, a mail is sent in which there is no reference of the voter with the numerical data of his vote, it would be a kind of "hard copy" of each vote. For the use of this system the mailbox of the voting officers must be enabled so that it does not reject the mails as spam.
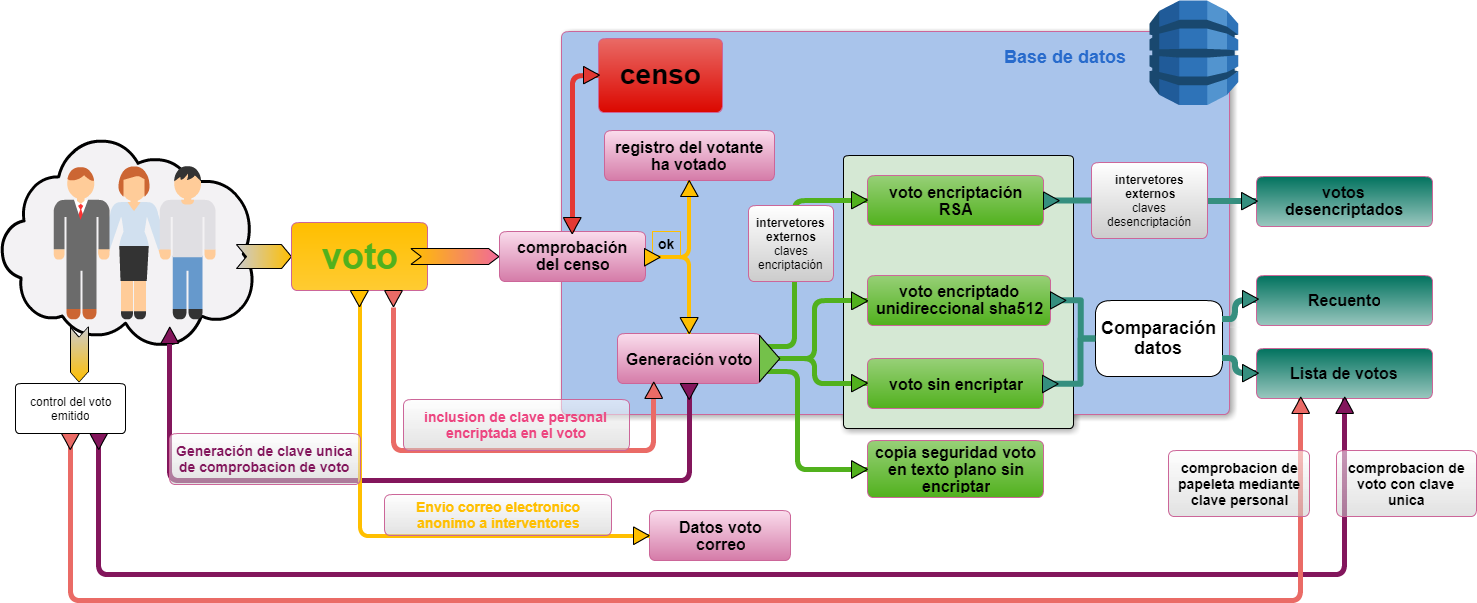
Throughout the voting process the vote is not encrypted asymmetrically on the client computer because it can have several drawbacks including attacks by "Man-in-the-middle", so it is recommended to use secure SSH servers for the information to travel encrypted.
Some people consider that the data must be encrypted in the client to avoid that a malicious administrator can modify the code and capture the data of the votes, this is completely ridiculous because if there is a malicious administrator could change the code so that the client sends double data, encrypted and unencrypted. (In any case this would be solved with the possibility of being able to audit at all times the code that is running on the server by independent programmers).
One of the methods implemented in demokratian for the verification of the integrity of the vote by the voter (individual verifiability), is that at the end of the voting process, the system delivers a unique alphanumeric key that the voter can save so that later, when the voting is finished and all the votes that have been used in the tally are listed, the voter can verify that his vote is there.
Another method (it can be enabled at the choice of the administrator) is that the voter, when he is performing the voting process, enters a password of his choice (the system ensures that it is unique), which is encrypted in a unidirectional way (it cannot be decrypted) and once the voting process is finished, when the results are public, he can enter his password to check that his vote is correctly registered.
Any computer system is as a rule insecure, it depends largely on the integrity of system administrators, whatever measures are implemented to secure it.
Other voting systems "trust" everything to complicated encryption systems, but even with asymmetric or double key encryption systems there are the same vulnerabilities to the illegal inclusion of votes, since the public keys, which encrypt the vote, are accessible at all times on the server, or chain of servers if mixnet type systems are used, which are more designed for obfuscation.
Usability of the application
One of the characteristics of the application is that we have tried to make it very easy to use, both the installation of the software and the management of the platform by the administrators, and the use by the voters. In addition, the programming language used, PHP, and the database, MySQL, means that it can be installed on most web servers.
The voter user, when accessing can see the active votes, there may be several active votes and from different constituencies, a voter of Malaga can be asked for the electoral list of his province (only registered voters of that province vote), and at the same time by the head of the national list to be voted by registered voters throughout Spain, he could even be voting for a decision of his people to which obviously only registered voters of that population would have access.
In addition, the application also allows the creation of working groups by general, regional or provincial constituencies that can be closed, requiring the authorization of the group administrator to access, or open.
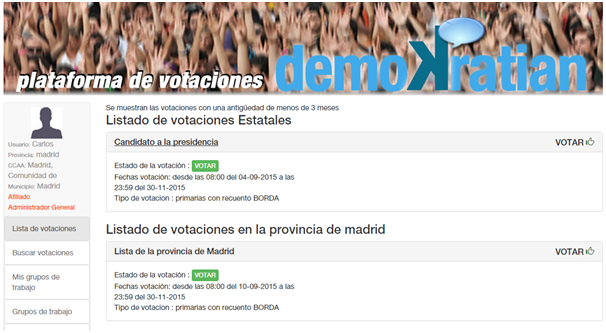
The way to vote depends on the type of count chosen, in weighted systems the list of candidates must be ordered, to maintain parity (if it is a parity election) two lists are chosen, having to choose the same number of candidates of the male gender as of the female gender. If it is not a parity election or what is chosen are options, only one list will appear.
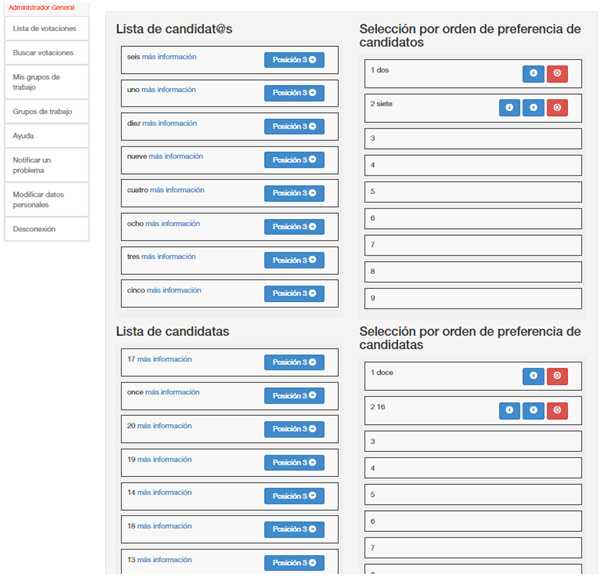
For the administrator, the application is just as easy to use.
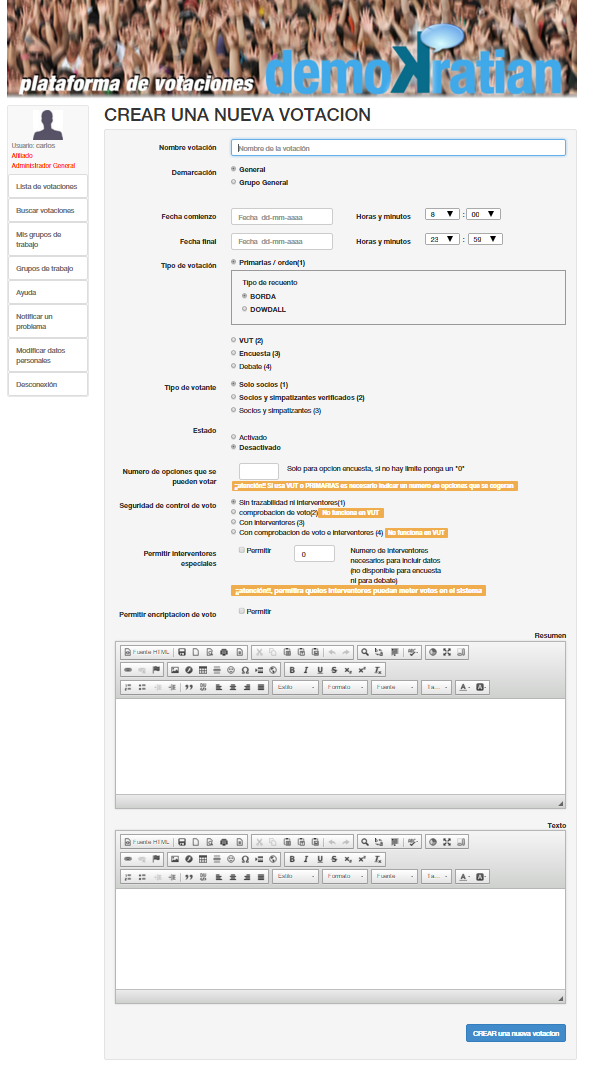
The creation and/or modification of a vote is done through a form in which the necessary data must be filled out
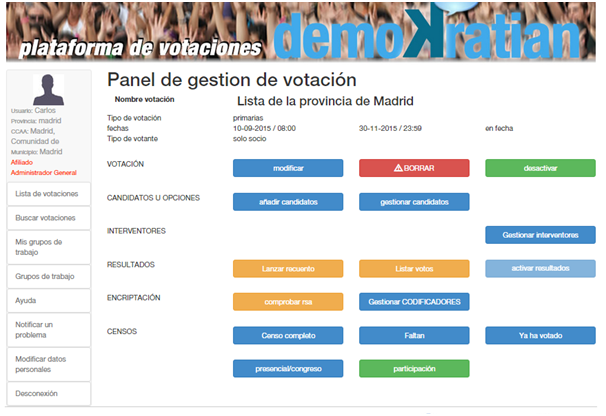
Voting is administered through a control panel that allows the management of the different options in a very simple way.
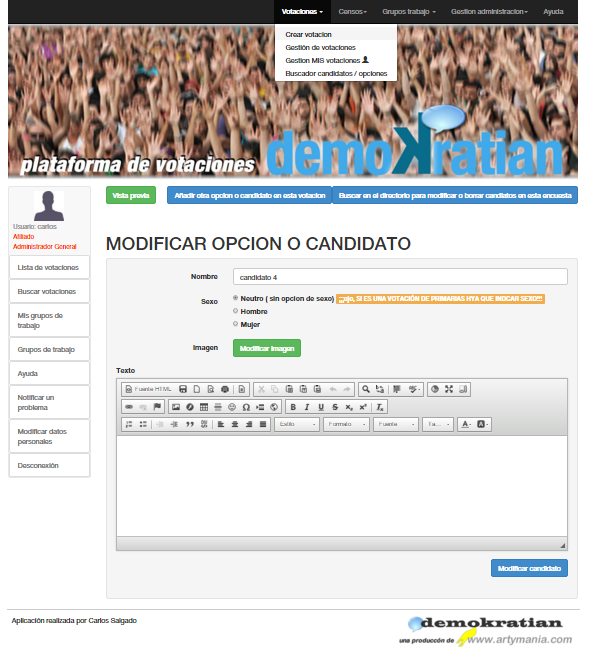
To add options or candidates can also be done through a simple form that also allows you to upload and crop an image that you want to be displayed in each option or candidate.
In the same way, there is a module that allows the management of the censuses of the application, adding or modifying voters massively, or one by one.
Other systems that it incorporates is the blocking of registered voters so that they cannot vote, with several options, for example, if they are going to vote at the ballot box, or if they are going to participate in a congress and are going to exercise their right to vote there, etc.

